At Oktane in May 2018, VMware and Okta announced a strategic partnership to deliver advanced identity capabilities for the Digital Workspace. By integrating VMware Workspace ONE and the Okta Identity Cloud, our customers can easily and securely move to the cloud, adopt best-of-breed technologies and simplify IT management.
Since this announcement, VMware and Okta have worked closely to build a proven integration between both solutions.
The integration between both solutions allows the end user to enrol their device into Workspace ONE UEM using an Okta account. The user is then able to access their enterprise catalog of applications published from Okta. Conditional access can also be configured such that a user must enrol their device into Workspace ONE UEM to access critical applications.

Pete Lindley’s blog details the integration of Workspace ONE UEM and Okta, including a number of videos of the user experience.
There are a number of guides available which detail the integration of both solutions.
- Configure Conditional Access Policies in Workspace ONE with Okta – link.
- Integrating Okta: VMware Workspace ONE Operational Tutorial (Techzone) – link
- Advanced integrations with Okta: VMware Workspace ONE – link
- Okta – Provisioning Users Into Workspace ONE by Charlie Hodge – link
Recently, I’ve been working with clients who did not have any on-premises Active Directory. Their corporate directory was the Okta Identity Cloud. The purpose of this article is to detail the configuration settings I used to enable this integration.
Please note: That since writing this blog article, VMware and Okta have developed integration between Workspace ONE and Okta so that users/groups can be synchronised from Okta to Workspace ONE. Please see the following three articles by Steven D’Sa (VMware) on how to integrate both solutions.
- Workspace ONE – Okta Integration Part 1: Core Setup and Configuration – link
- Workspace ONE – Okta Integration Part 2: Unified Digital Workspace – link
- Workspace ONE – Okta Integration Part 3: SCIM Provisioning – link
As of October 2020, Charlie Hodge from VMware UK wrote this excellent article on how to integrate both solutions and enroll a Windows 10 Out of the Box Enrollments (OOBE) too. See Windows 10 Azure Enrolment with Okta Directory & Workspace ONE.
The article I wrote below is still useful on how you would previously integrate both solutions, but the users are JIT’ed into Workspace ONE UEM and Access.
The integration guide I followed a the time was titled Integrating VMware Workspace ONE with Okta (Beta) (Since removed). The latest official guide titled Integrating VMware Workspace ONE with Okta (as of August 2020) is available here.
I’ve detailed the additional steps as well as screen captures from the integration detailed below. For my customers, we Just-In-Time (JIT) the users from Okta into Workspace ONE UEM and Workspace ONE Access (previously VMware Identity Manager) as outlined below:

Federate Workspace ONE UEM with Okta
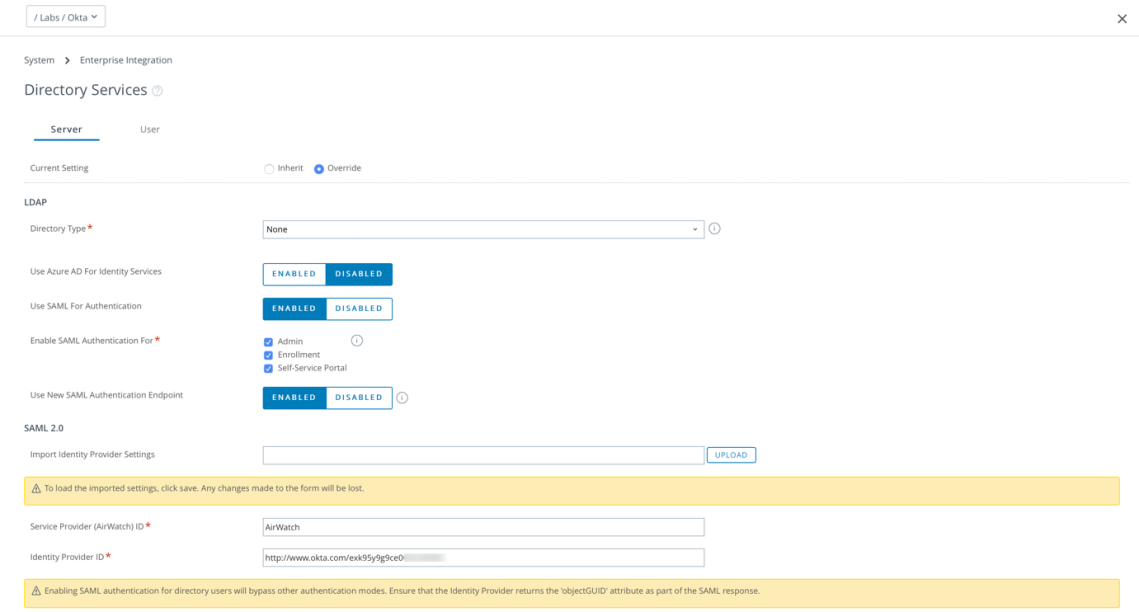
Following the integration guide outlined above, follow the steps outlined in Section “Okta as Federation Provider to Airwatch” from page 20 – 27. Below are some of the settings from my lab.
The Okta application settings are as follows:


Note the Audience Restriction is specified as AirWatch, which matches the Service Provider name in Workspace ONE UEM.

The Workspace ONE UEM (Airwatch settings) for my lab are as follows. Of course you’ll have specific tenant URLs to suit your environment.

When this integration is completed, you can now enrol your device into Workspace ONE UEM using your Okta credentials. You’ll note that your Okta userid is JIT’ed into Workspace ONE UEM too.

Federate Workspace ONE Access with Okta
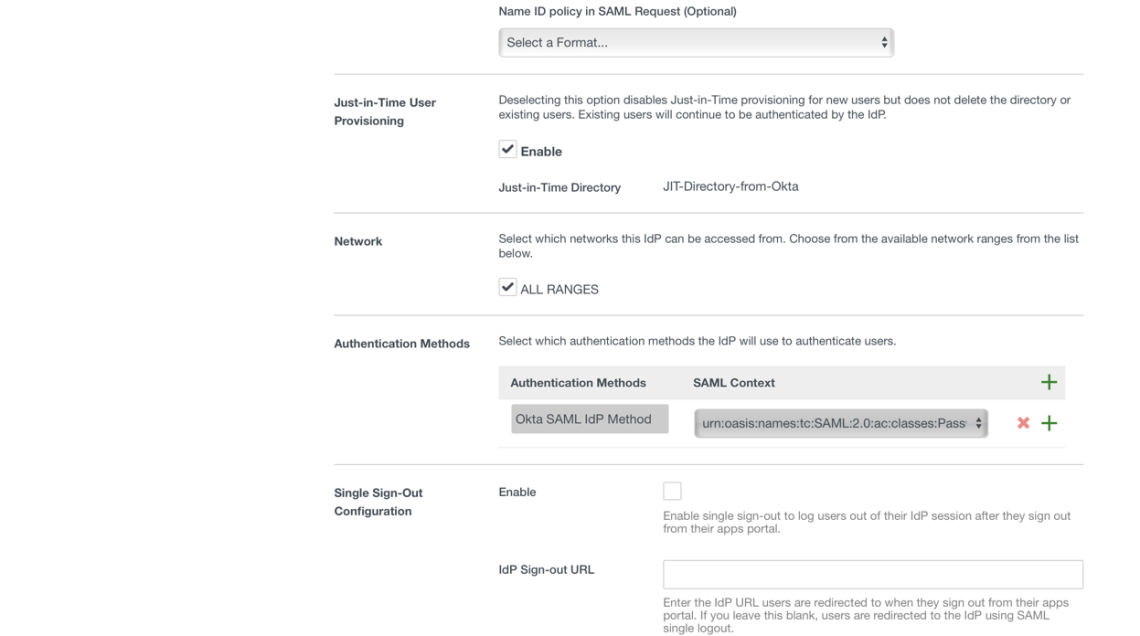
Now we’ll federate Workspace ONE Access with Okta. This time I used the Integrating VMware Workspace ONE with Okta (Beta) guide and complete the steps in Chapters 4 and 5.
The Workspace ONE Access settings from my lab are as follows:



The Okta Workpace ONE settings are as follows:
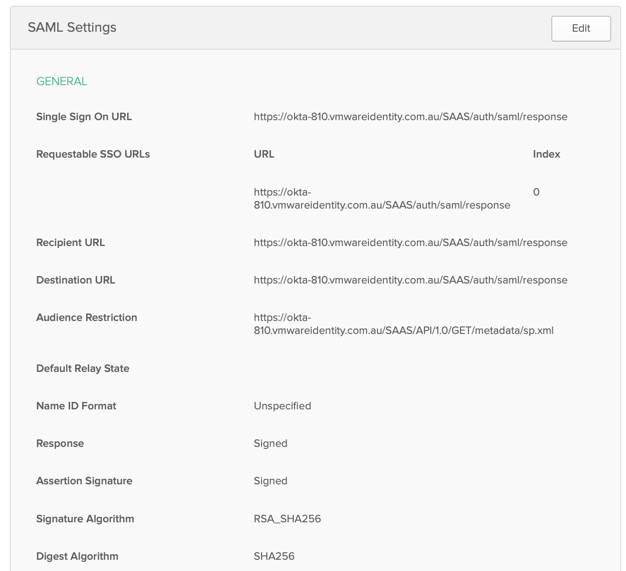
The attributes are particularly important to configure correctly:

Setup Single Sign-on with Workspace ONE UEM and Access.
Next follow the instructions in my previous blog article to setup SSO within Workspace ONE Access for your devices of choice. In my lab, I tested iOS, Windows 10 and macOS.
For mobile SSO to work with iOS we need to have UPN prefix (without @domain.com) as the Kerberos Principle name. The attribute might be provided to Workspace ONE UEM as username@companyname.org. However this profile will fail to get installed on iOS (as the Kerberos attribute is incorrectly formatted. ie. username@companyname.org@vmwareidentity.com). The best way to resolve the issue is to create a custom attribute for Lookup Value in Workspace ONE UEM and use that as the Lookup value in SSO profile for Kerberos Principle name. Thanks to Renan Medina (VMware) for providing this solution, of which the settings are shown below:
- Navigate to Groups & Settings – All settings
- Navigate to Device and Users – General
- Click on Lookup Fields
- Click on Add Custom Field. Enter details as follows:

- Now for the iOS SSO settings, change the Kerberos Principal Name to {KerberosSPN}

Workspace ONE Access Policies
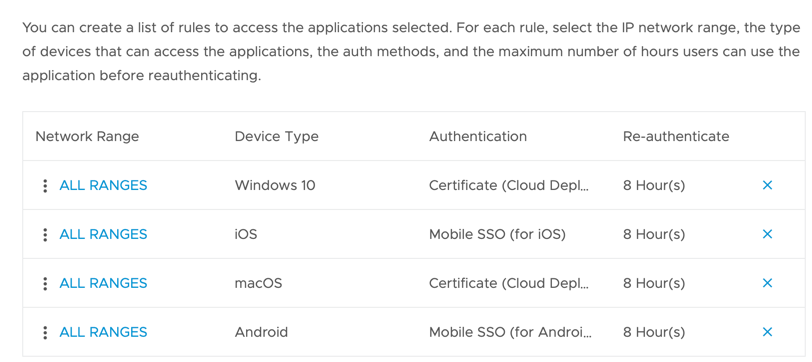
Now you can create an access policy so that by default users can login to the Workspace ONE Access Catalog by using their Okta credentials. For critical applications (such as Salesforce in my example below) they need a device to be managed (ie. enrolled into Workspace ONE UEM) and have a certificate provisioned to the device.

The default access polices are detailed as follows:

The managed devices policy is detailed as follows:

Note now only the certificate based authentication methods are available with no fallback method. Therefore a user can only access these applications if their device is enrolled into Workspace ONE UEM.

That’s it ! You’ve integrated both solutions. Good news that in the coming months, an adapter will be available which will synchronise users from Okta to Workspace ONE via a SCIM adapter. This integration will be detailed here.
Darryl
Addendum
5 January 2020 – Whilst watching this informative video WS1 Access Series Episode 03 – Integrating with 3rd party IDP, Mobile SSO Zero Trust/SASE Model, they referenced this great documentation on integrating Workspace ONE Access with Okta by Mazhar Warsi.
